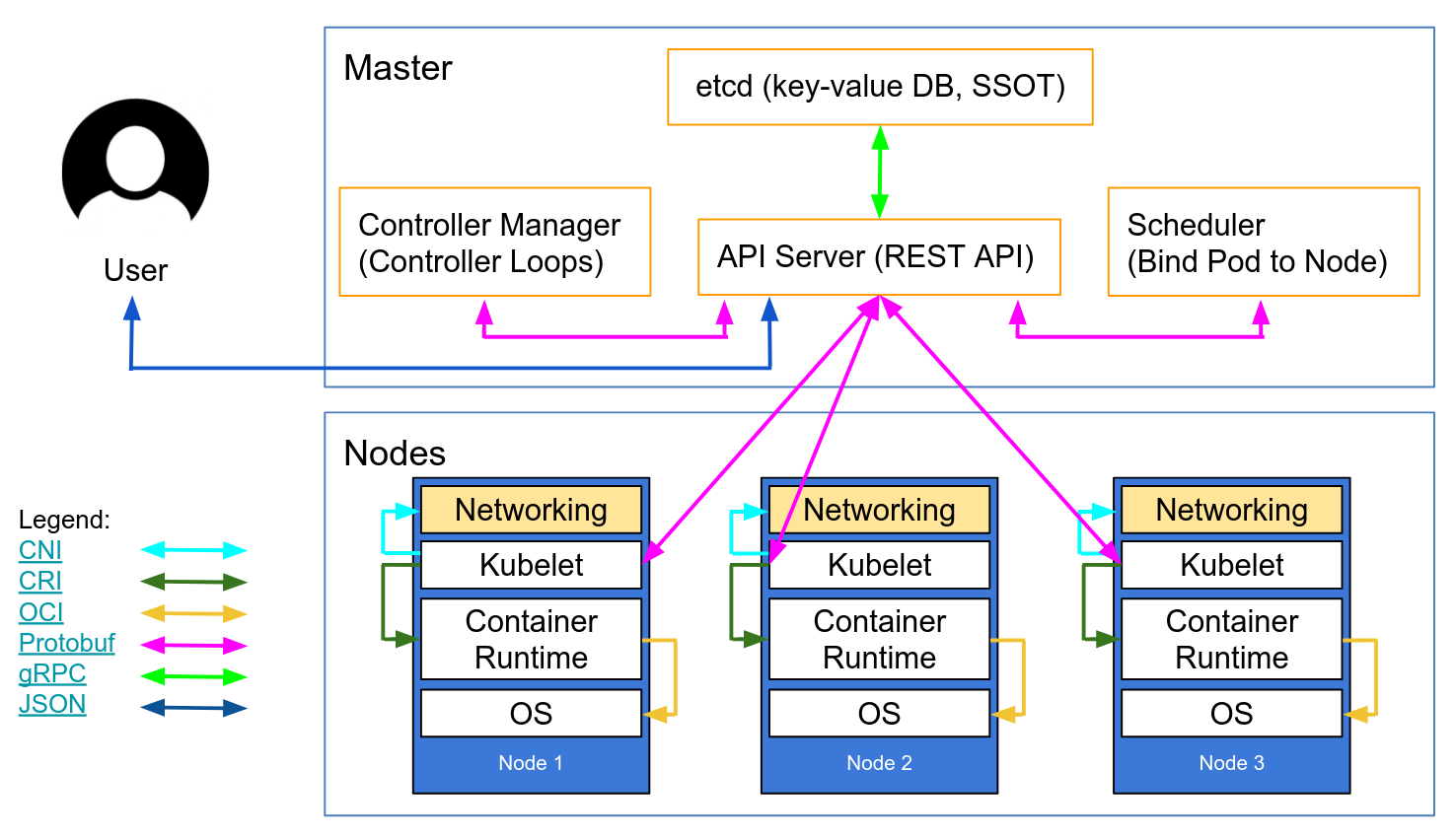
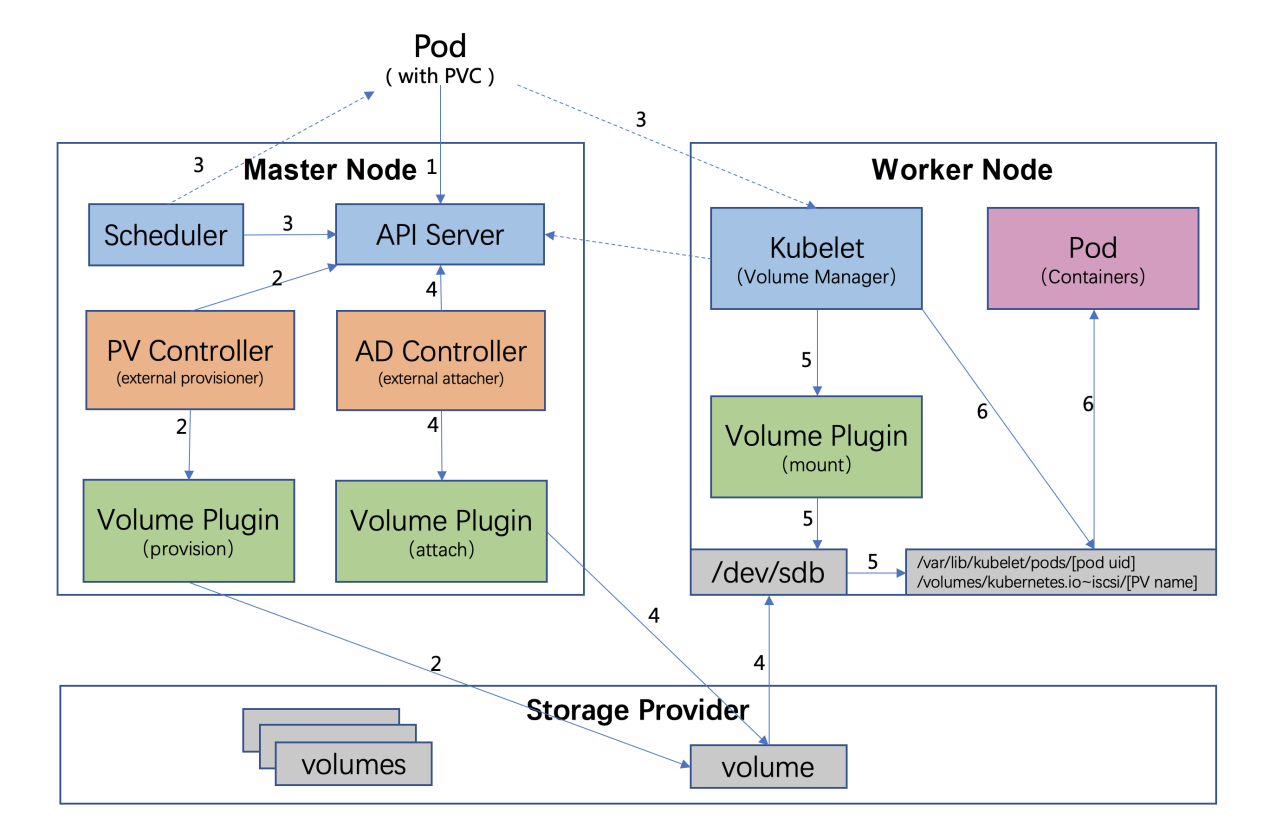
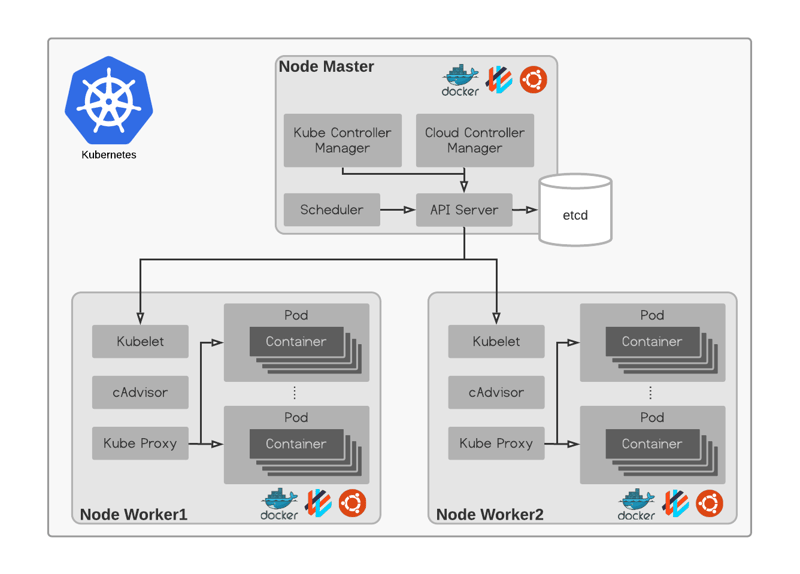
Hierarchical structure of Deployment, ReplicaSet, and Pod (adapted from... | Download Scientific Diagram

Mastering Kubernetes Pods Troubleshooting: Advanced Strategies and Solutions | by Paddy Adallah | AWS Tip

Kubernetes.io Blog: The Future of Cloud Providers in Kubernetes - General Discussions - Discuss Kubernetes
GitHub - kubernetes/k8s.io: Code and configuration to manage Kubernetes project infrastructure, including various *.k8s.io sites
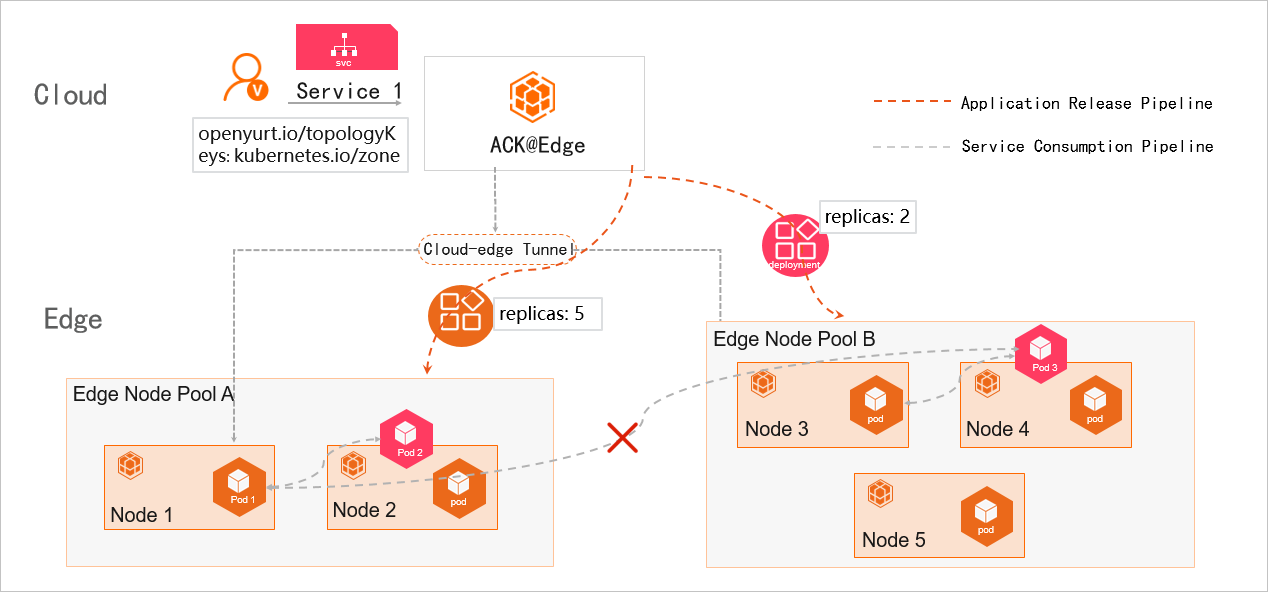
Configure a Service topology - Container Service for Kubernetes - Alibaba Cloud Documentation Center
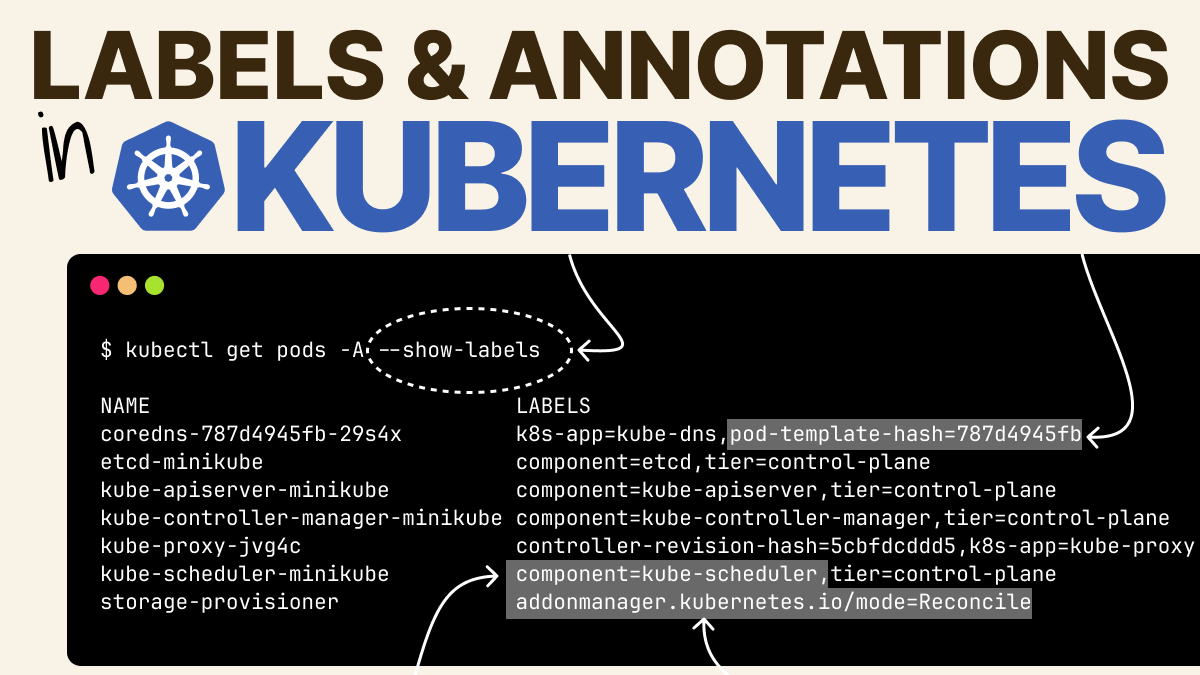
Daniele Polencic — @danielepolencic@hachyderm.io on X: "In Kubernetes, you can use labels to assign key-value pairs to any resources. Labels are ubiquitous and necessary to everyday operations such as creating services. However,